In previous post I’ve describe how it is possible to use Docker in order to setup a Docker environment to study Yet Another Stars Rating wordpress plugin https://wpscan.com/vulnerability/9207.
Here I am going to show you how you can configure a vulnerable environment by using Docker Security Playground .
Docker Security Playground installation
Install DSP is described here.
When you have installed all the dependencies, you can run it by using:
npm start
Creation of vulnerable scenario
Creation of wordpress docker image
I started from https://github.com/khaledsaikat/wordpress-php56-docker to create a wordpress docker image with all installed.
In DSP, I have used Dockerfile image editor to create the image:
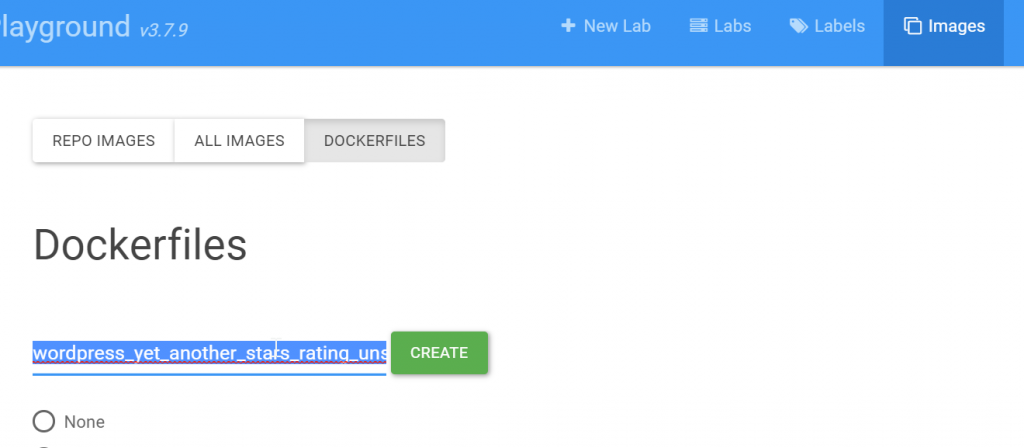
I started from this:
https://raw.githubusercontent.com/khaledsaikat/wordpress-php56-docker/master/Dockerfile
But I changed WordPress version (< 5.5.2 ) to bypass WordPress security fix of vulnerable. I use the following repo:
https://github.com/DockerSecurityPlayground/dsp-images
to build my DSP images.
WordPress with vulnerable plugin has the following Dockerfile:
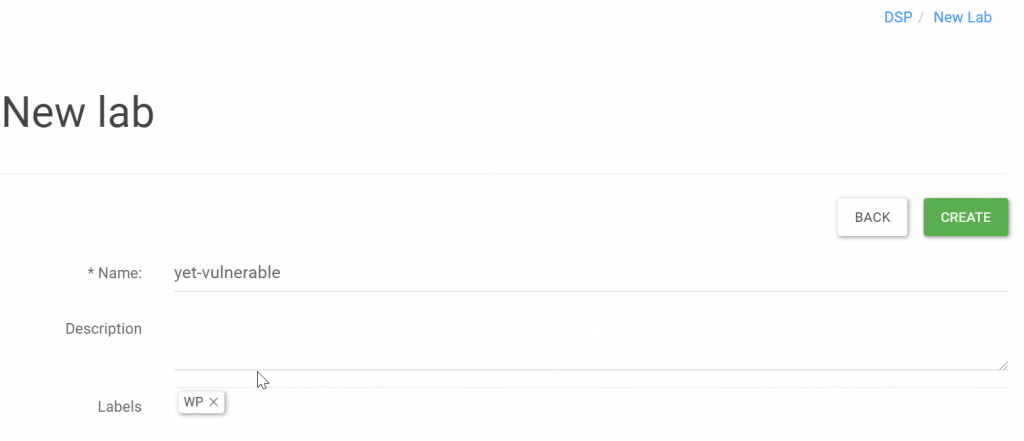
Create DSP lab
I have created the vulnerable lab:
Create network:
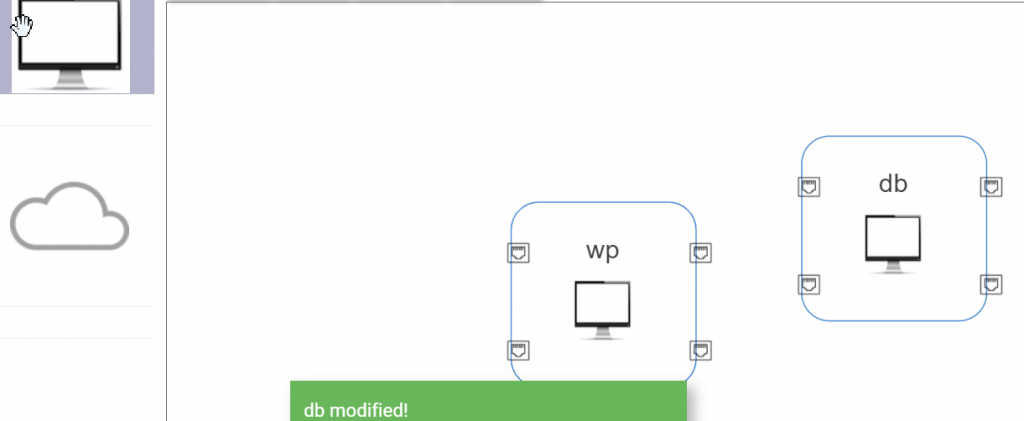
Set the docker images for DB and WP:
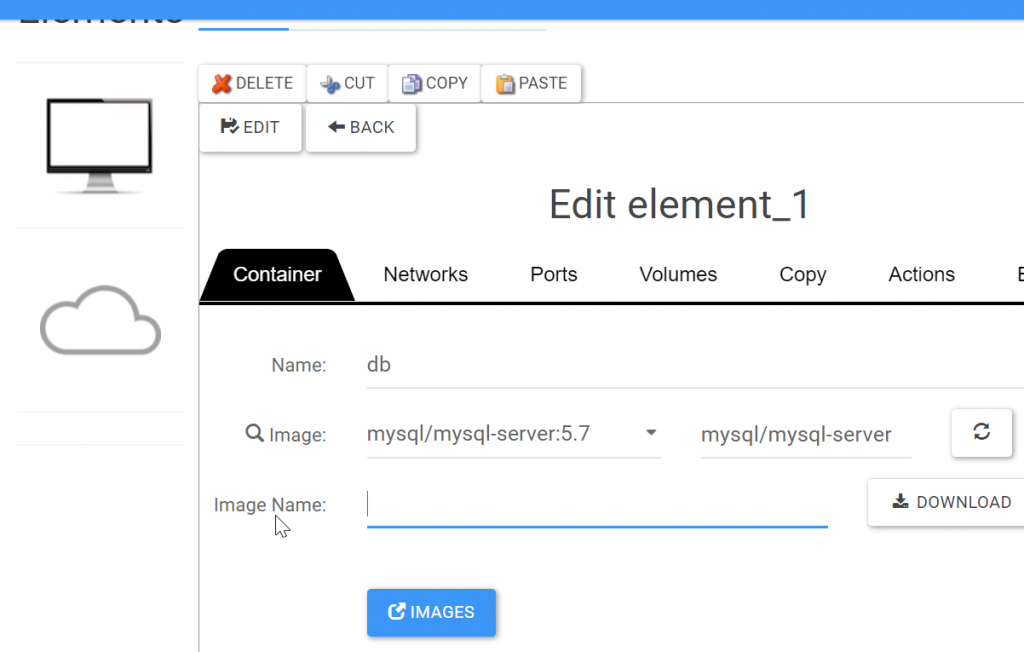
Set environment variables as follows by using DSP edit container:
environment: MYSQL_ROOT_PASSWORD: rootpass MYSQL_DATABASE: wordpress MYSQL_USER: wordpress MYSQL_PASSWORD: wordpresswordpress: build: context: . args: WORDPRESS_DB_HOST: db:3306 WORDPRESS_DB_NAME: wordpress WORDPRESS_DB_USER: wordpress WORDPRESS_DB_PASSWORD: wordpress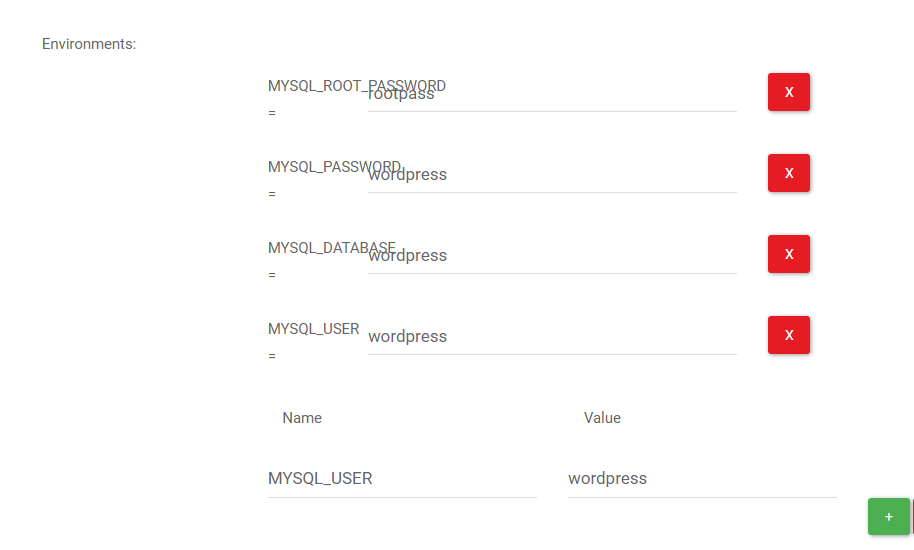
PS. we need to improve this interface!!
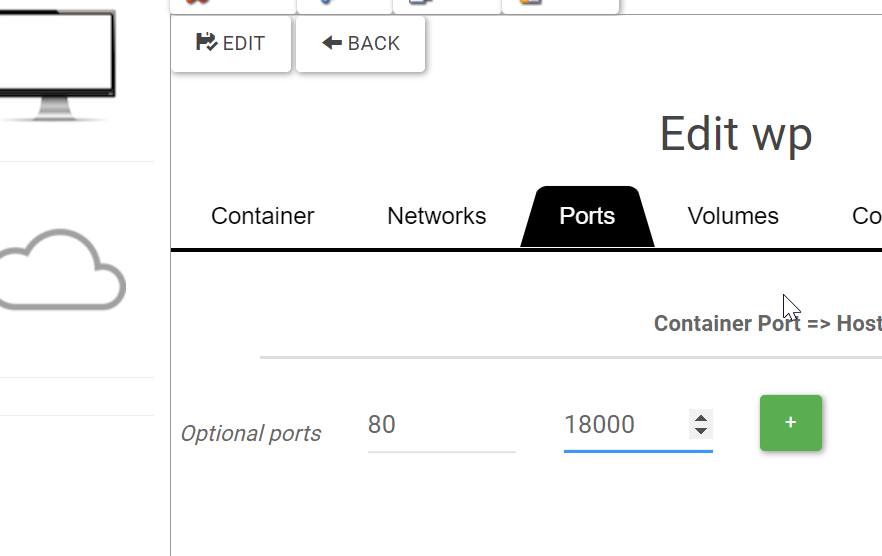
Forward apache port 80 to a port (18000)
Database initialization
Once installed, we have to configure WordPress and create a persistent database storega.
We can persist database storage in wp init-entrypoint , as suggested by docker mysql doc by using docker-entrypoint-initdb.d directory:
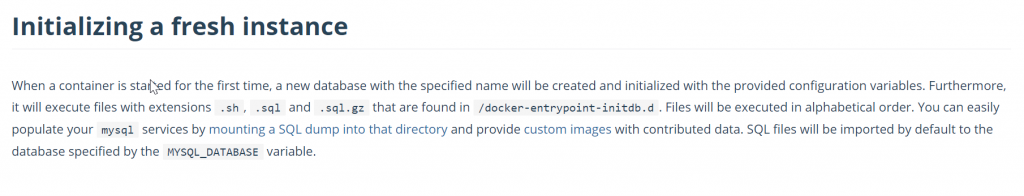
To do this we have to:
- access to internal docker container
- dump database with mysqldump
- extract database and put in a directory
- binding the internal volume /docker-entrypoint-inittdb.d with a database
We can do it in DSP:
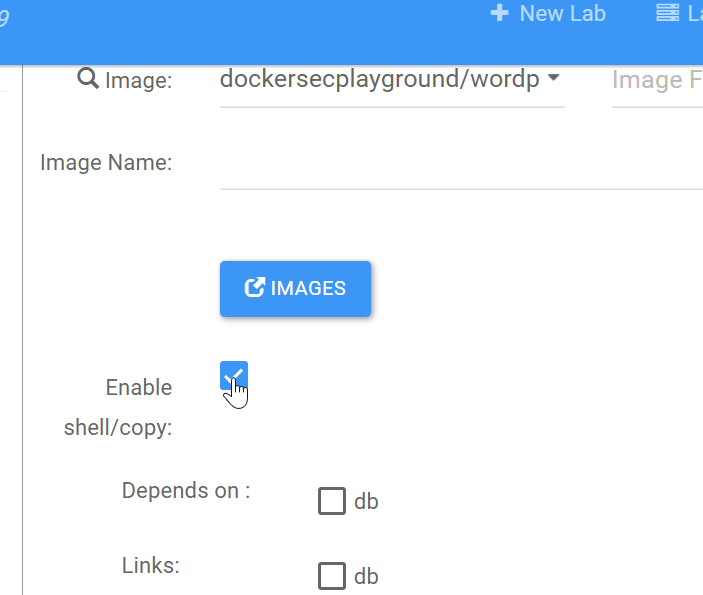
enable shell for WordPress container
Right click on container in canvas, and checkbox Enable shell:
Configure WordPress
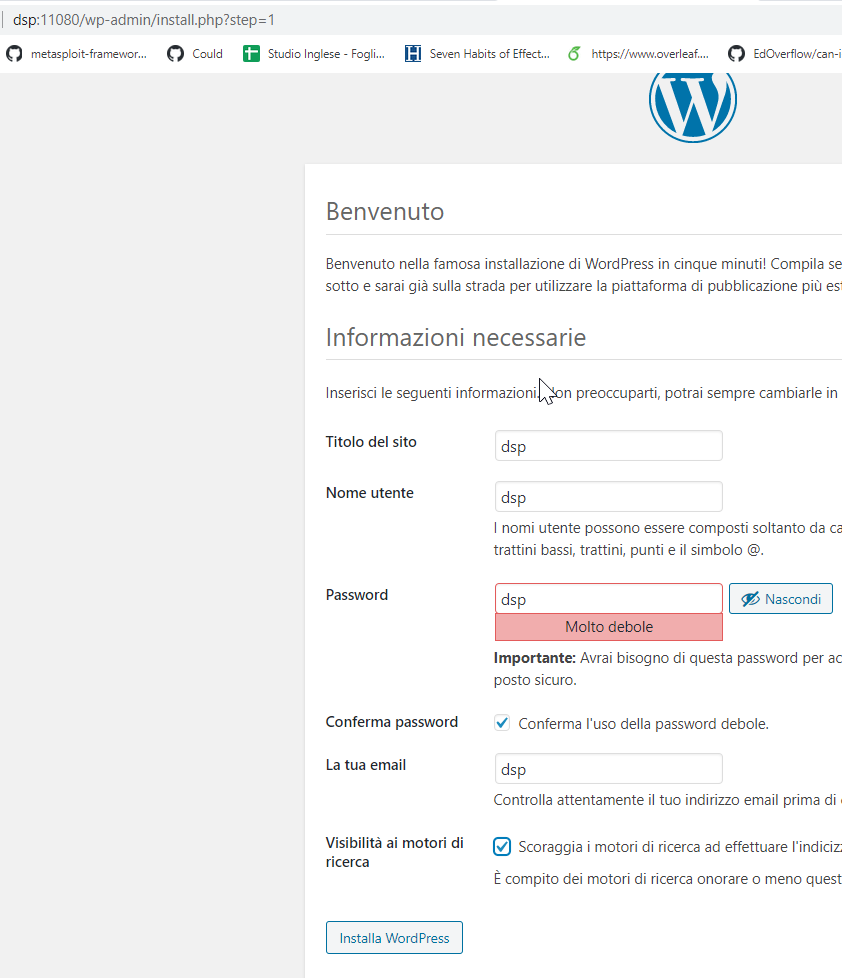
I usually use dsp/dsp as credentials for all dsp vulnerable services services.
Once that wp is running, I can configure other conditions to exploit the vulnerability: the vulnerability occurs when an user uses yasr_visitor_votes shortcode. So, I create a WordPress post containing this shortcode:
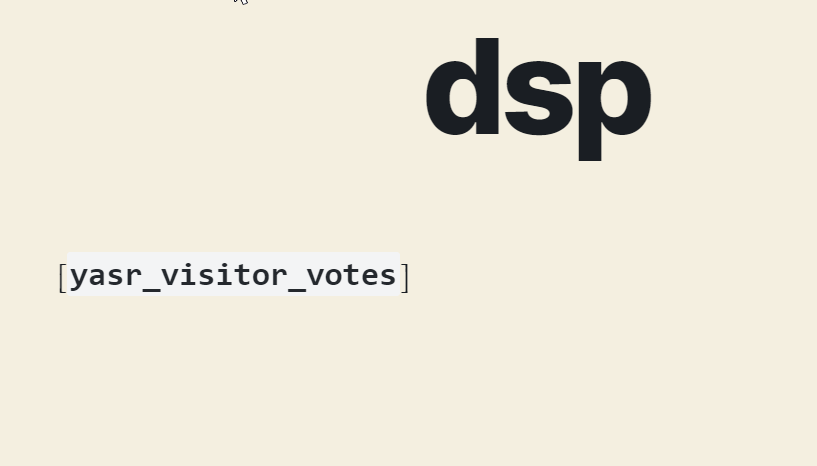
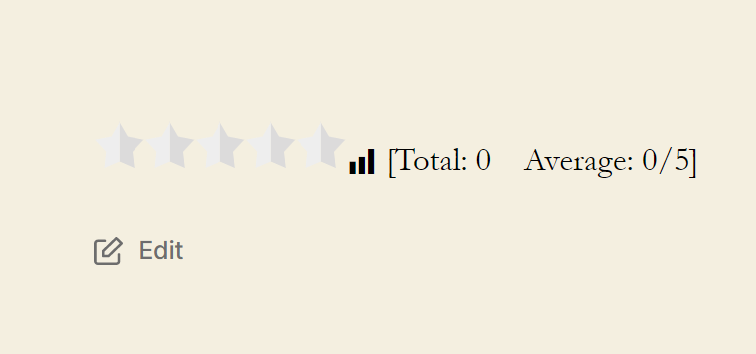
Now plugin is taken:
Persistent configuration
Then, you can navigate WordPress terminal in container “Network Elements”:
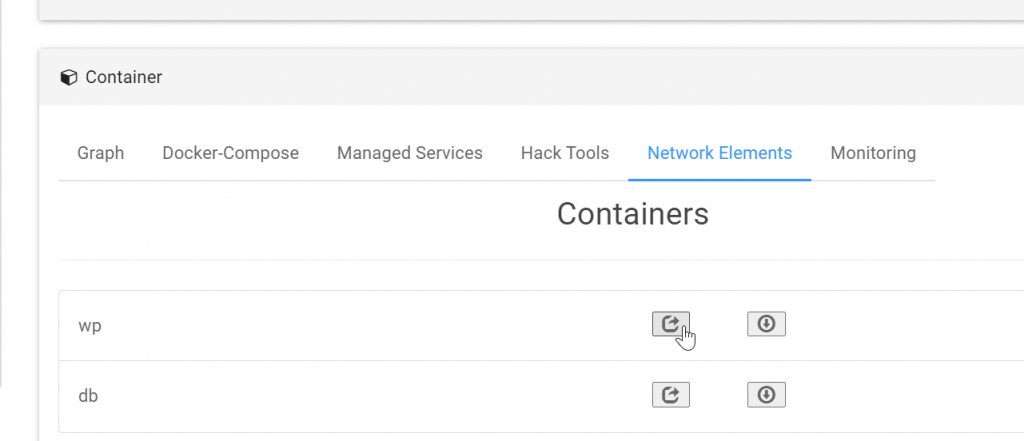
I can dump the database by using the following command:
mysqldump -u root -p wordpress > /root/dump.sql
password is rootpass
I can download the dump and create a volume entrypoint in network configuration of dsp:
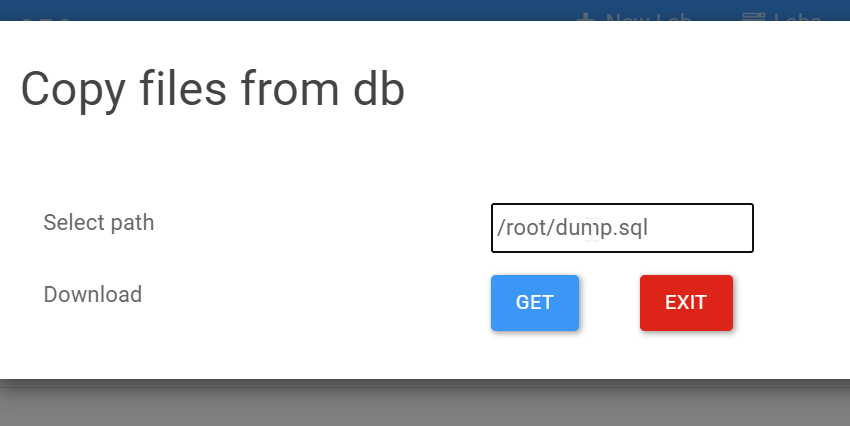
Now we add a Volume entrypoint configuration in dsp: Click on DB container and bind /docker-entrypoint-initdb.d to a database folder of DSP:
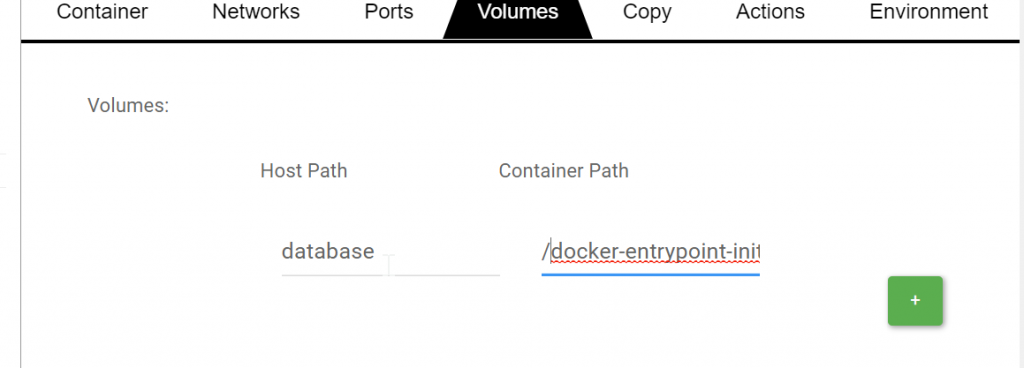
DSP automatically creates a new directory under ~/dsp/<user_dsp>/<lab_name>/database:
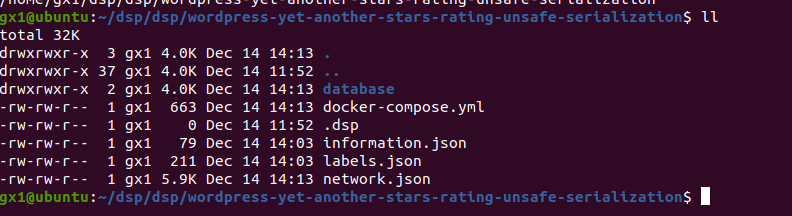
Now we can upload dump.sql inside :
Restart:
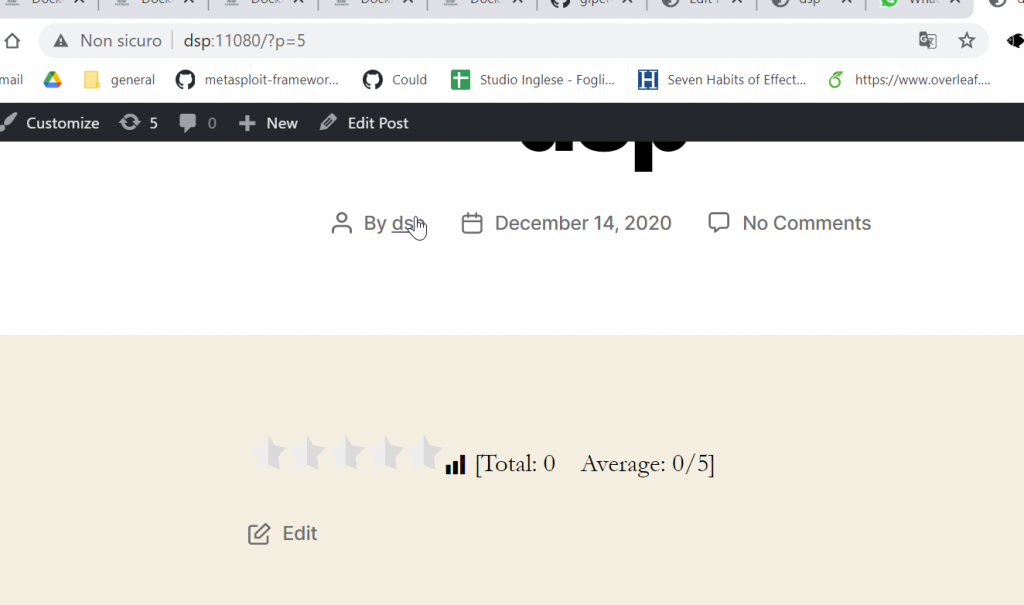
Everything Works! Now you can hack it.
Security is SecSI !