In the evolving landscape of cybersecurity, phishing attacks continue to present significant risks to users and organizations alike. This article delves into a sophisticated phishing campaign that manipulates GitHub’s mention mail notification system for phishing attacks, highlighting the cunning methods employed by cybercriminals. It serves as a cautionary tale, underlining the necessity for vigilance and the adoption of robust security measures. Let’s start from the beginning.
This morning I woke up with an email from GitHub that seemed pretty accurate:
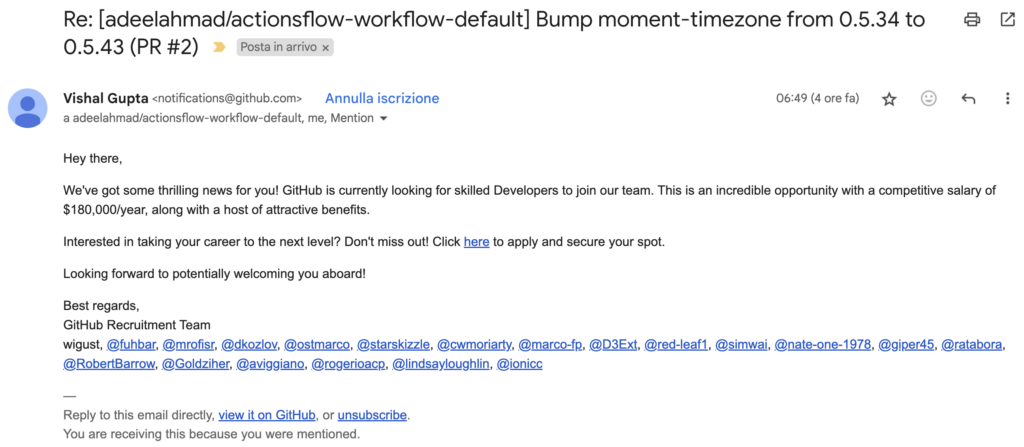
It seemed a mail from GitHub, and at the first glance I did not realize that it was a phishing. However, (even when I recover from my sleep), I analyzed it better.
Discover the phishing attempt
The “here” link pointed to:
https://githubtalentcommunity.githubcareers.online/ # THIS IS MALICIOUS
There are difference indicators of the presence of a phishing attack.
Evidence #1: googling
By googling it is possible to observe that the real domain for Job careers at Github is github.careers
Another indicator is looking for “Job fraud attacks via GitHub”. There are several relevant issue related to phishing attacks through fake GitHub job alerts.
Evidence 2: domain lookup
A quick search of the domain let me to discover that the domain was hosted on a EC2 AWS instance subjected to several abuses:
GitHub does not use AWS but has its hosted servers.
Furthermore, if you perform a whois request at the GitHub domain, you can obtain a lot of relevant information about the organization:
The malicious domain did not belong to GitHub.
This confirms my suspects. After the discovery, I quickly notify the other users, then I analyzed the attack.
Analyze the attack
The attack involves two steps:
- email issue notification mechanism that is able to send a mail from the real GitHub address “[email protected]” through the email issue notification mechanism that sends you an email when you are mentioned inside an issue.
- OAuth mechanism to obtain privileges on your personal GitHub account
Phishing attack
By a quick analysis, the starting username was vishalgupta1987.
This user adds a comment to an automatic PR performed from autobot, a service to automate the update of packages on GitHub:
“Re: [adeelahmad/actionsflow-workflow-default] Bump moment-timezone from 0.5.34 to 0.5.43 (PR #2)”
The attackers added an issue to the pull request #2 that triggers an email notification against our accounts
What happens if you have been phished?
GitHub quickly disabled the account, but the email is still present in our mailboxes, the domain is still active, and the impact can still be dangerous:
- Integrity: The most dangerous permission is DELETE REPO: by accepting, you allow to DELETE any of your repository
- Authentication: the application is able to create internal discussions in place of the real user by potentially compromising other users
- Confidentiality: the application can read each internal repository (even those related to the teams)
The attacker tries to obtain privileges on your GitHub account by using the OAuth mechanism, which is used to allow external applications to use resources on behalf of the user. It is a very useful approach to integrate external systems with another application, but it can be pretty dangerous if the external system is not trusted (such as in this case).
After the attacker adds the issue in the pull request:
- GitHub notifies the victim about the opened issues that were mentioned to you.
- If the victim clicks on the link, he/she is redirected to the malicious website
- The malicious website redirects the victim to the GitHub OAuth permission page
- GitHub asks to grant the following permissions:
The request leverages the OAuth mechanism to obtain the following permissions from GitHub:
- repo user read:org
- read:discussion
- gist write:discussion
- delete_repo
- If the victim clicks on “Authorize confirmautorizan” he/she is giving those permissions to the attacker
- The attacker owns the personal repos of the victim.
How did I responded to the incident?
Actually, I proceeded with the following steps:
- Notify GitHub to suggest to check the account that is has been using for performing phishing attacks
- Send a spam abuse to whois about the malicious domain
- Notify the GitHub users that they were victims of a phishing attack. The fastest approach to notify them is… using GitHub! I have created a repository with an issue mentioning users under attack. In this way, through the same attacker mechanism, I have notified the users.
Who was attacking?
Unfortunately, it is not possible to assert that the user exploited to send the issue was the real attacker or he was a victim of a previous attack. In fact, it is possible to use the GitHub REST API https://docs.github.com/en/rest/issues/comments?apiVersion=2022-11-28#create-an-issue-comment–fine-grained-access-tokens to automate the creation of issues.
After an hour, GitHub removed the vishalgupta1987 account:
However, it seemed to be an active account; the attacker probably hacked the username and used it as an entry point for the phishing attack. Hope that GitHub will enable it after the incident response.
Countermeasures
Unfortunately, it is impossible to protect ourselves against this attack because it exploits the flexible features of GitHub repositories. However, it is possible to use some countermeasures:
- Even if it does not protect against comments’ abuse, you can opt for a “signature check” for commits (see Protected Branches)
- If your projects are critical and sensitive for the company, you could opt for a local Git instance and use GitHub for public projects and personal projects. You can use several interesting alternatives, such as GitLab or Gitea
- You can set up a SecDevOps process that checks for user commits and issues to respond to such incidents (contact us for more details).
- Follow the best practices provided by GitHub to harden your account.

